A global high-performance network
We currently maintain data centers at six locations in Europe, the US, and Asia.
All our data centers are optimized for reliable, top performance and are perfect for web application and database hosting, gaming / gameservers, audio and video streaming, and much more.

Speed Test
Check your download speed from all available velia.net data center locations
Frankfurt (DE)
Deutsche Telekom*
Lumen*
Twelve99*
DE-CIX* / AMS-IX* / LINX*
Test IP: 85.195.64.252
Strasbourg (FR)
Deutsche Telekom*
Lumen*
Twelve99*
DE-CIX* / AMS-IX* / LINX*
Test IP: 92.42.106.3
* via our own European backbone
DDoS Protection
Denial of Service attacks can threaten your infrastructure and harm your business. In recent years, DDoS attacks have become more frequent, more powerful and more difficult to mitigate.
At velia.net, we use a multi-layer approach to protect your servers against possible DDoS attacks.
Traffic Monitoring & early DDoS detection
Our gold standard Arbor Peakflow SP traffic monitoring system analyses all incoming traffic to our network. It is set-up to detect DDoS attacks within seconds.
Depending on type and size of the detected attack, several mitigation measures are activated.
Traffic Management
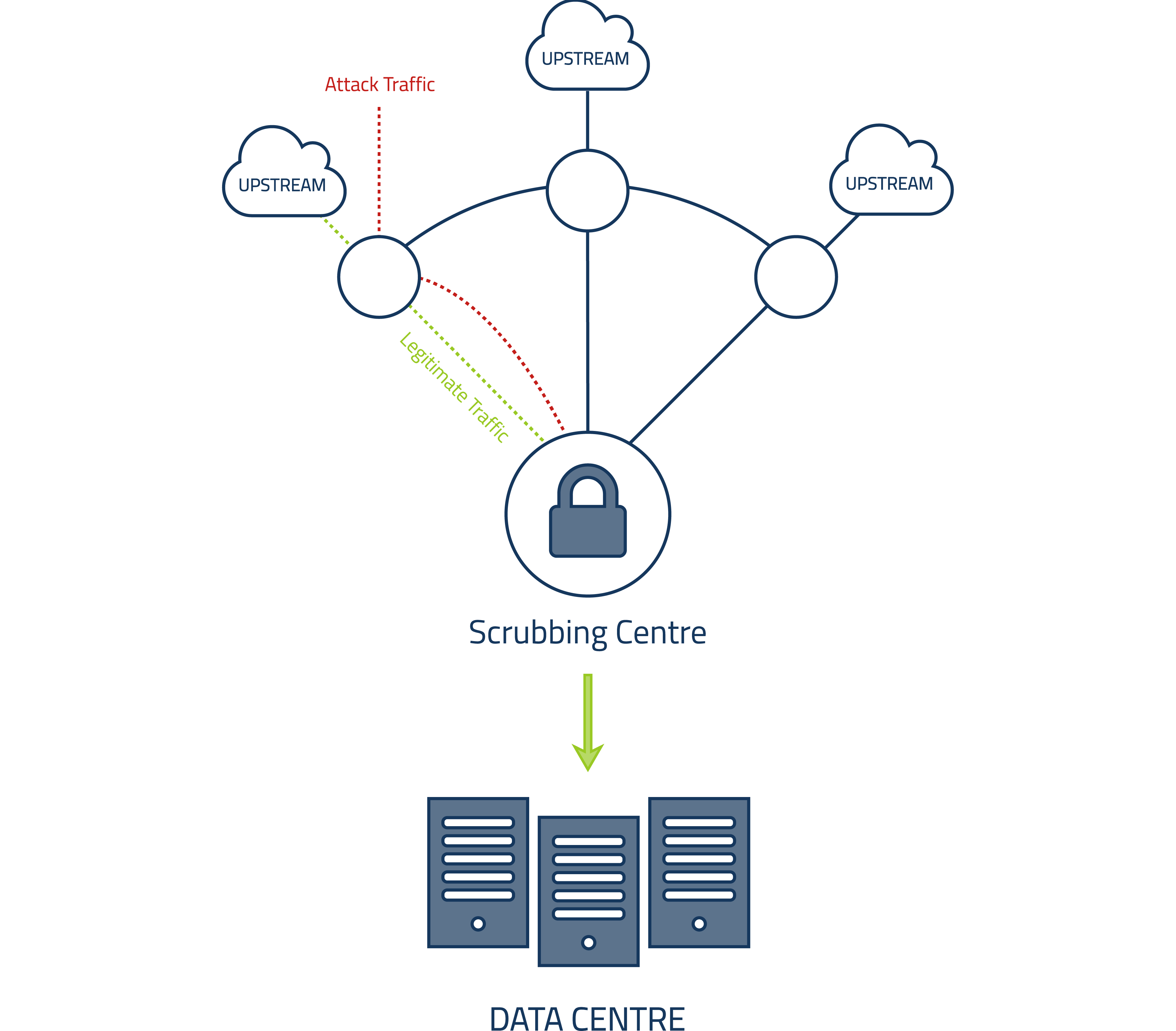
The core of our defence are "scrubbing centers". These are distributed across all of our data centers so that attacks can be mitigated at key parts of our network.
Malicious traffic is filtered / dropped before coming into the core network, while clean traffic is forwarded to its appropriate destination.
These scrubbing centers are tuned to detect different attack patterns. With advanced recognition algorithms, they keep false positive and false negative rates as low as possible.
We are using appliances from multiple vendors, including RioRey.
Threat reduction
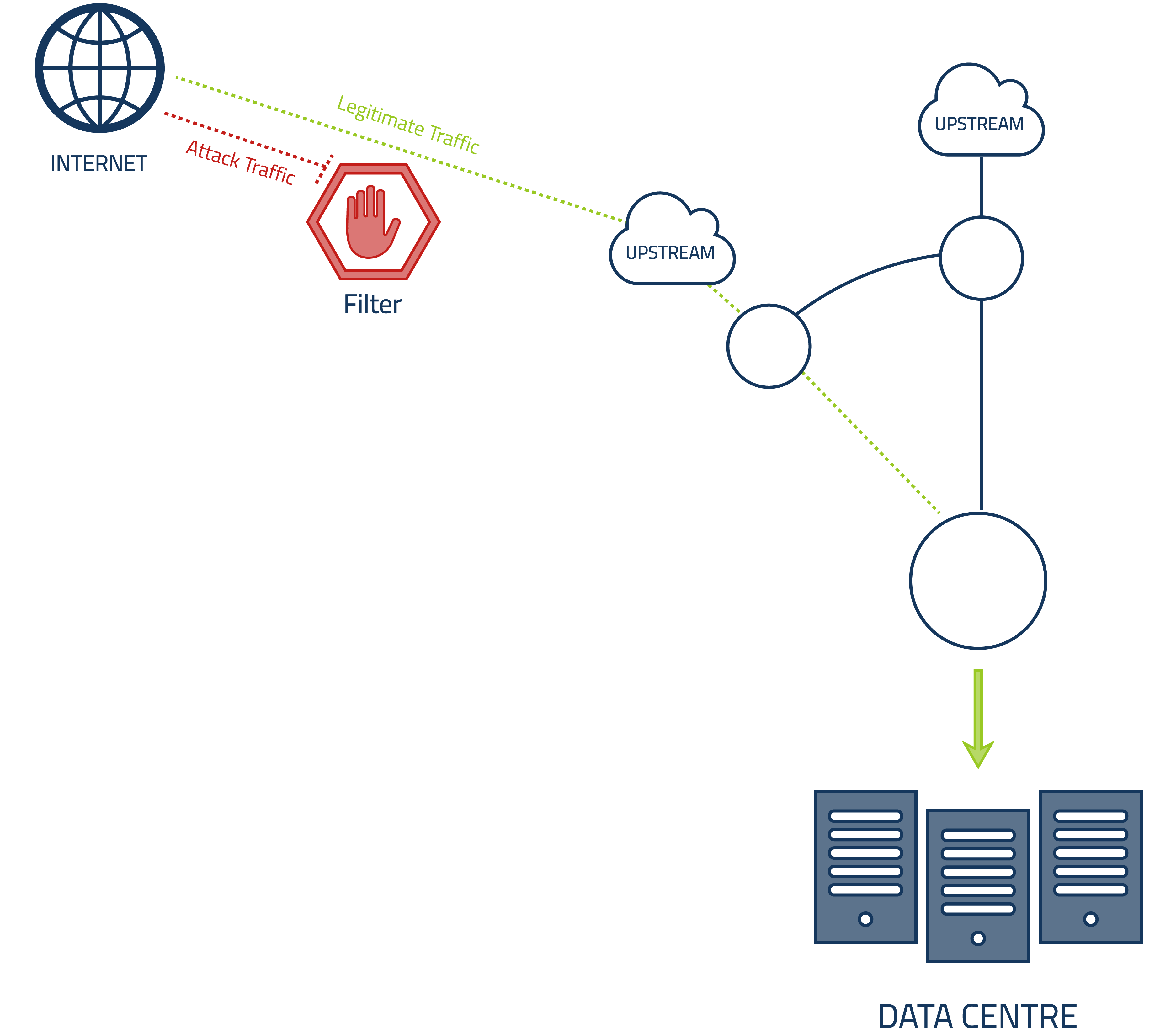
In the event of larger attacks, we use filters and rate-limiters at our network border to reduce or even block an attack. These filters and rate-limiters are centrally initiated and managed, and then applied automatically to all of our border routers.

Pre-empty traffic block
The next layer are so-called "Remotely Triggered BlackHoles" where we can advise our upstream providers to drop traffic matching certain patterns to keep our network clean.
This means, attack traffic doesn't even reach our border routers. We only use upstream providers offering such a service.

